Secure Boot
Athena Arch supports Secure Boot in UEFI. Its deployment is managed automatically by Aegis installer that will detect if the system is UEFI and will create the proper certificates and sign the boot and kernel files needed for this process.
Key Enrollment
Section titled “Key Enrollment”The ISO Live Environment must be currently run with no Secure Boot. When Athena OS Arch-base is installed, the user must enable Secure Boot from BIOS settings.
At first reboot, it gets a MOK (Machine Owner Key) request for enrolling the Secure Boot certificate previously created for you by Aegis.
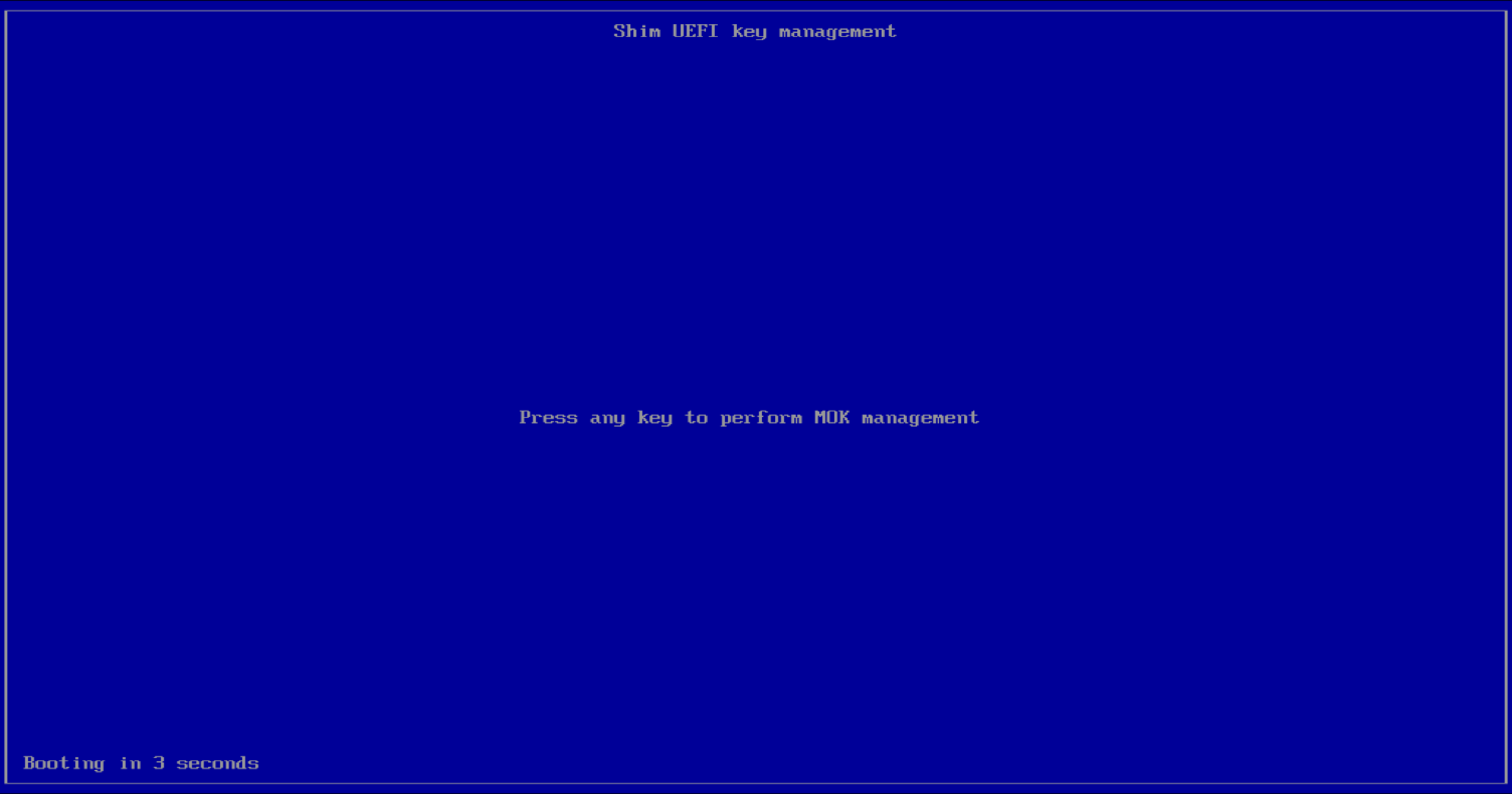
Press any key on your keyboard, and then select Enroll MOK.
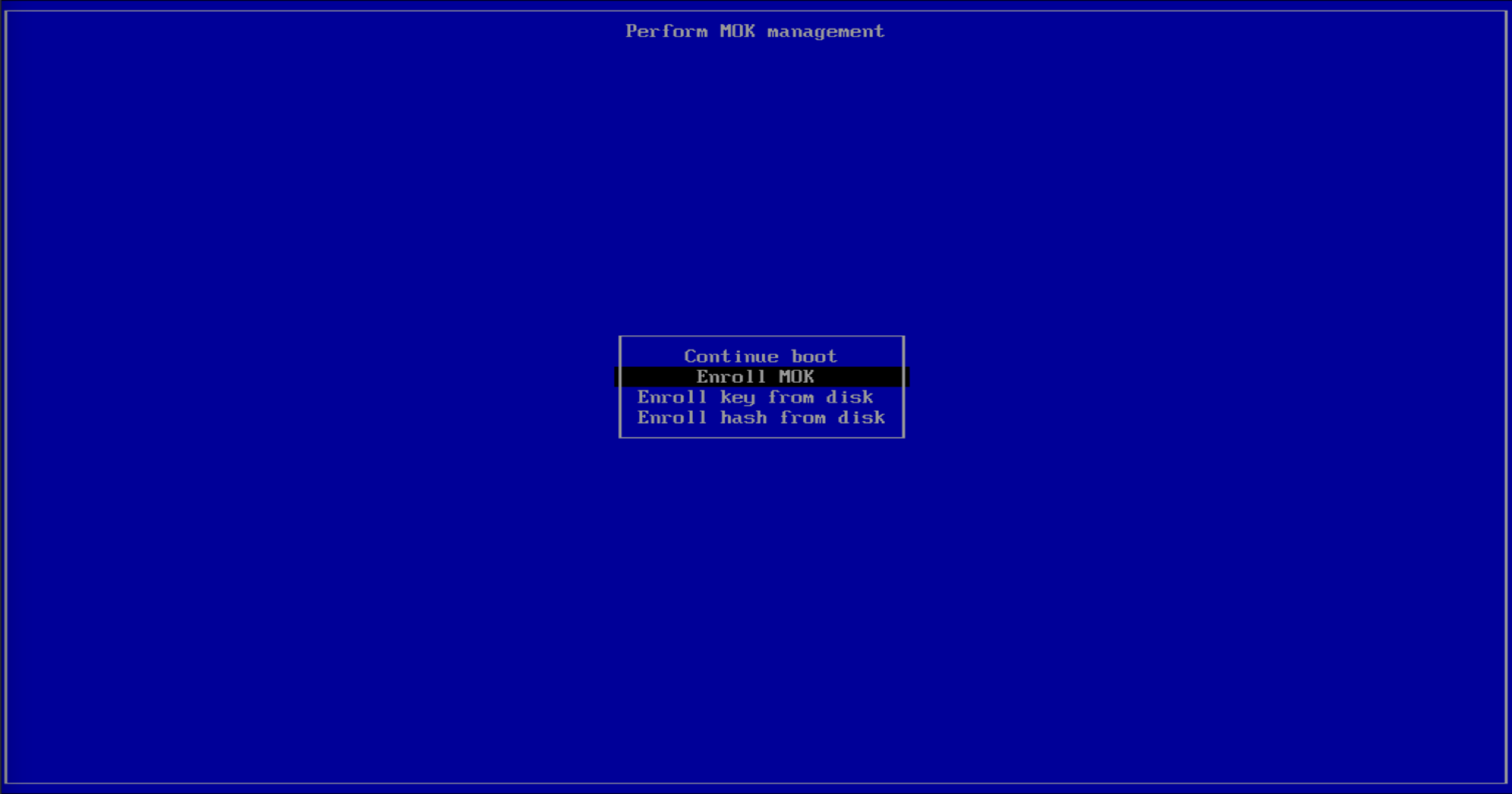
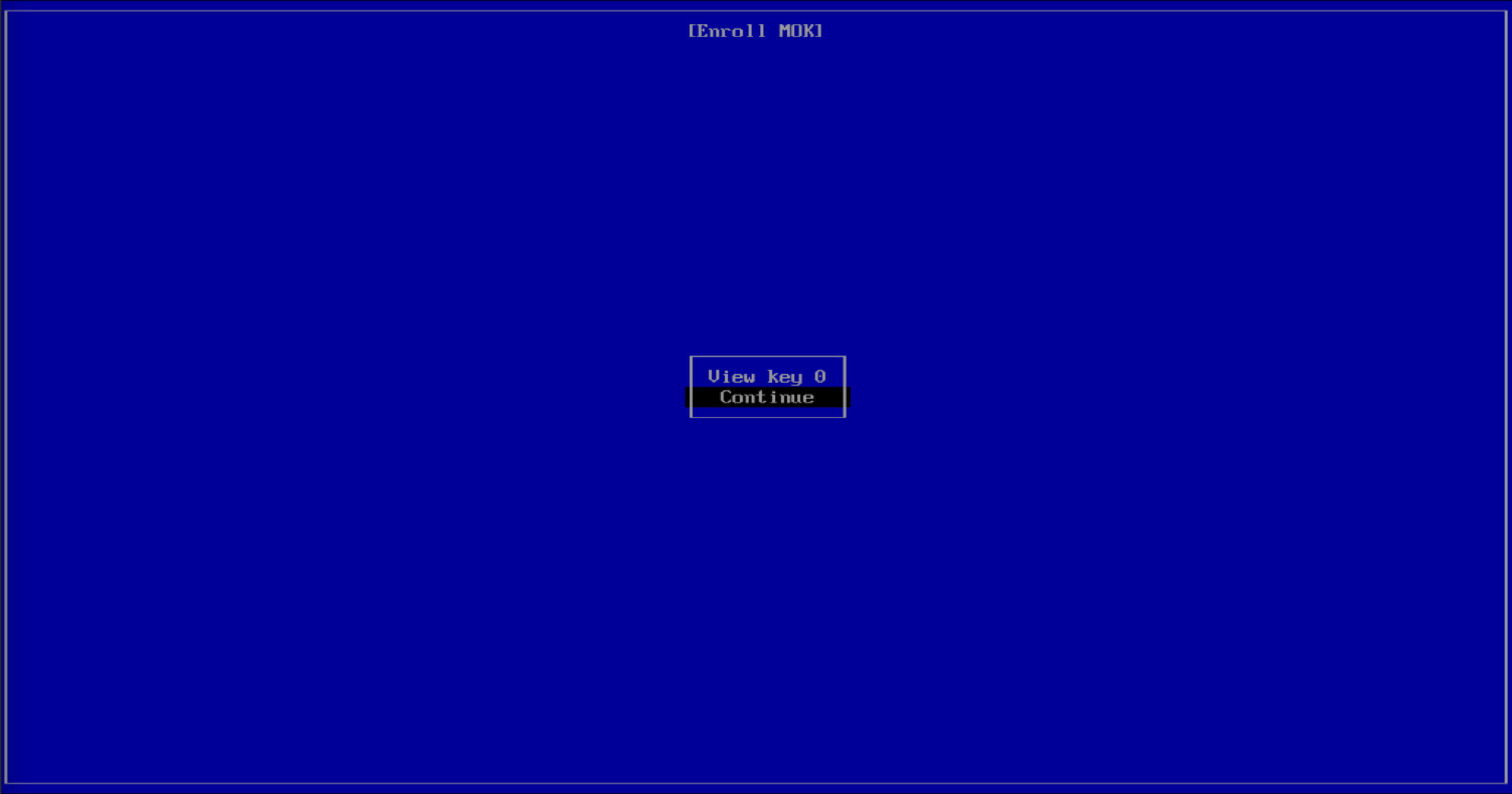
Press on Continue.
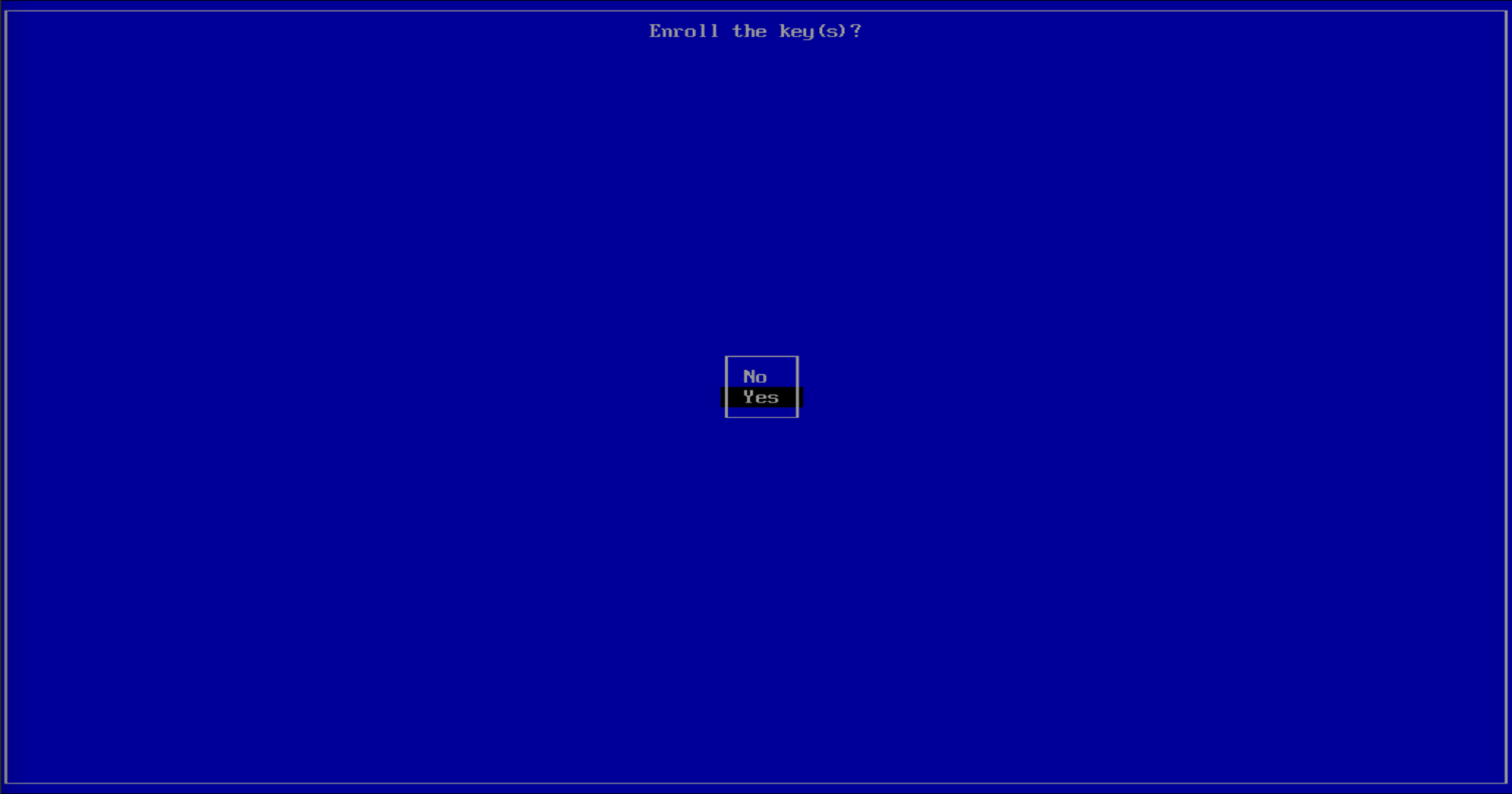
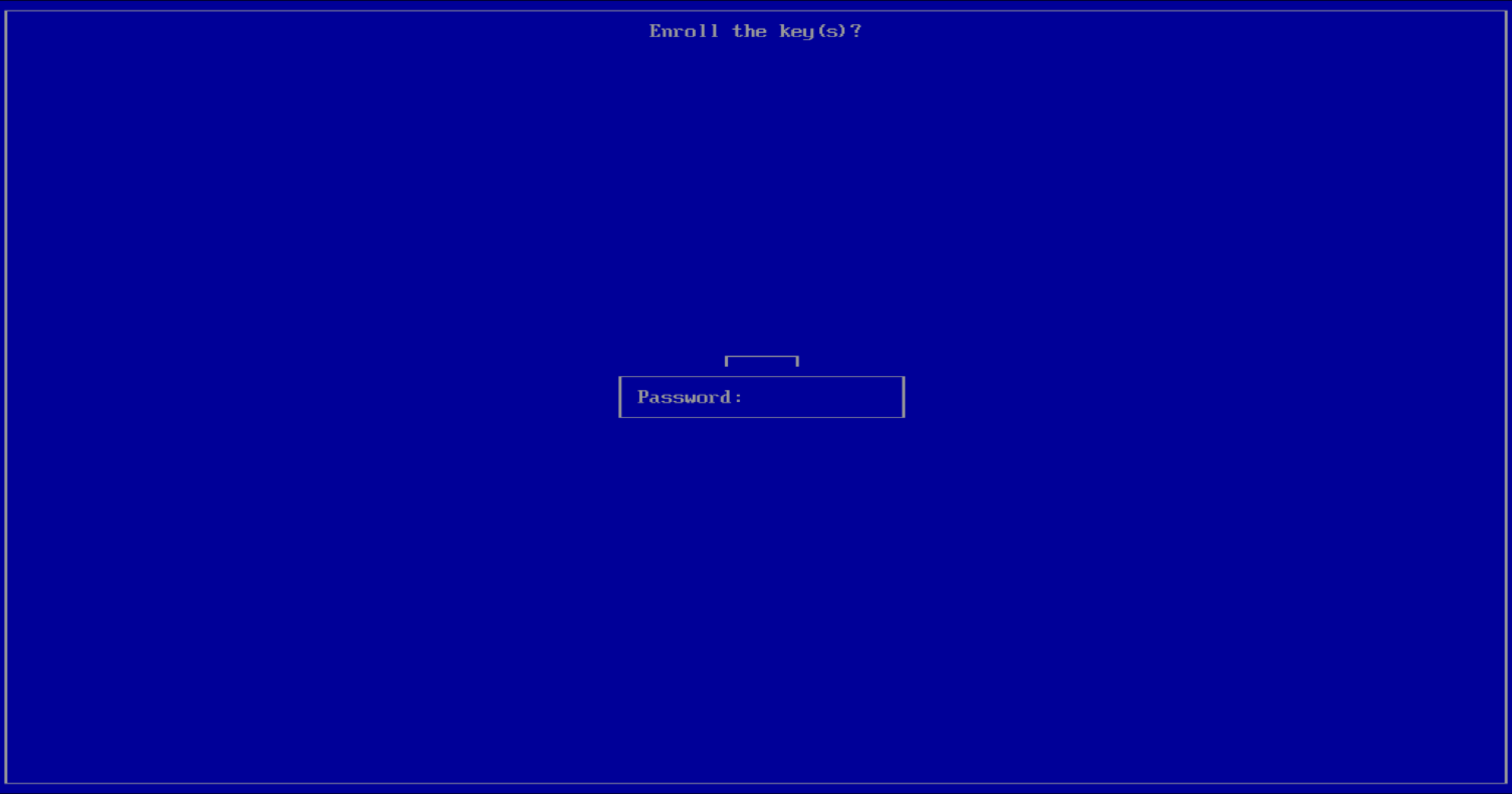
Press on Yes to confirm the enrollment.
Insert the root password you defined during the installation.
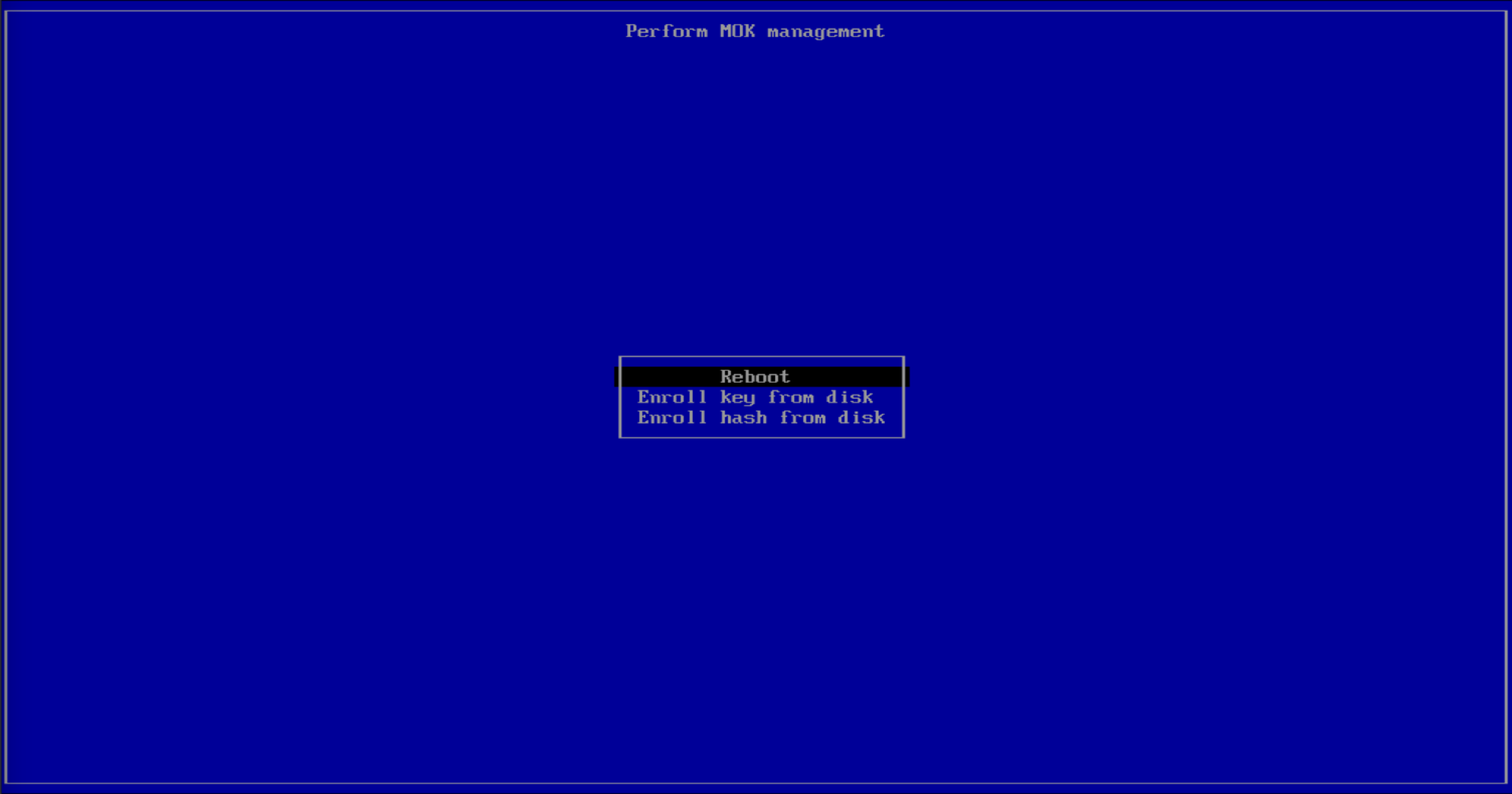
Finally, select Reboot.
After reboot, you should be able to access to Athena through Secure Boot.
Once you land on Athena environment, you can remove the MOK certificate from EFI partition:
sudo rm -rf /boot/efi/EFI/MOK.cerFile Revalidation
Section titled “File Revalidation”During the updates of packages involving kernel and GRUB, files signed by Secure Boot key could change and be not valid and trusted anymore. So, they need to be signed again.
Athena OS performs signing automatically for you, but in the worst scenario these files are not re-validated, and at boot you get an error like policy violated, you can boot by ISO Live Environment, mount the root and boot partitions to their proper mount points and running:
sudo arch-chroot /mnt
sbsign --key /etc/.secureboot/keys/MOK.key --cert /etc/.secureboot/keys/MOK.crt --output /boot/vmlinuz-linux-lts /boot/vmlinuz-linux-ltssbsign --key /etc/.secureboot/keys/MOK.key --cert /etc/.secureboot/keys/MOK.crt --output /boot/efi/EFI/GRUB/grubx64.efi /boot/efi/EFI/GRUB/grubx64.eficp /boot/efi/EFI/GRUB/grubx64.efi /boot/efi/EFI/BOOT/grubx64.efi