Red Team Menu
Red Team Menu is born for organizing in pretty manner the main pentesting tools that users need to start their hacking activity. It is deployed in different manner according to the installed environment.
In GNOME, it consists of two levels:
- 1st level containing several hacking categories, plus browser and VSCodium as editor
- 2nd level consisting of hacking tools deployed for each hacking category
Red Team menu can be accessed by CTRL+SPACE.
In details:
| Information Gathering | Dmitry | Nmap | Spiderfoot | TheHarvester | enum4linux | wafw00f | Fierce |
|---|---|---|---|---|---|---|---|
| Vulnerability Analysis | Legion | Nikto | unix-privesc-check | ||||
| Web Application Analysis | WPScan | Burpsuite | dirb | dirbuster | ffuf | Wfuzz | sqlmap |
| Password Attacks | John | Hashcat | Hydra | CEWL | CRUNCH | RSMangler | Medusa |
| Sniffing | mitmproxy | Responder | Wireshark | ||||
| Wireless Testing | Aircrack-ng | Kismet | Reaver | Wifite | Fern Wifi Cracker | Spooftooph | |
| Reverse Engineering | NASM | Radare2 | |||||
| Exploitation | SearchSploit | Metasploit | SEToolkit | ||||
| Post Exploitation | PowerSploit | Mimikatz | evil-winrm | proxychains-ng | weevely |
In Athena Arch, in all the environments, it reflects the classic menu layout in Linux. For example:
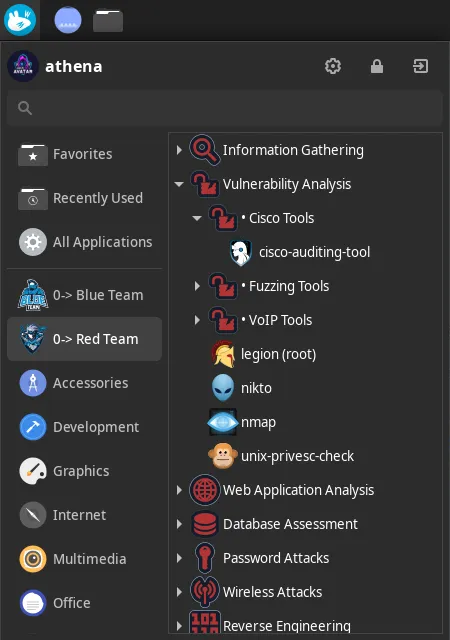
In Athena Nix, by Red Team menu, the tools are run in an ephimeral environment by Nix Shell. It means that once the user exits from Nix Shell, the tool is unlinked/removed. To keep a specific tool permanent on the system, you can set a Cyber Role or edit /etc/nixos/configuration.nix by adding explicitly the tool you need and run sudo nixos-rebuild switch.
At the beginning, these tools are not installed to avoid that users would store in the disk space installed tools or services that never use. For users that would like to get these main tools, the Enthusiast Student role must be chosen on the Welcome App.